Nowadays, due to the various existing technologies, we are exposed to a very intense and invasive scrutiny from governments or large companies. As we learnt from the revelations of former NSA Edward Snowden, several entities keep much of the Internet under full surveillance, violating the universal right of privacy. No wonder, several countries around the globe have strong data privacy laws – which, in this case, seems like putting the fox in charge of the hen house. And how can a blockchain change this privacy parameter?
A blockchain-based technology that functions as a layer of internet privacy, called mixnet, developed by Swiss startup Nym, promises to defend individuals from this constant surveillance on the Internet. It does so by hiding the so-called network traffic metadata on a blockchain with a bitcoin-like reward system, which ensures the project funding.
Projects that support and promote privacy and freedoms, for the most part, suffer from serious funding problems when they do not rely directly on donations. An example is the TOR project. The Nym project, on the other hand, is not only a new technological approach but also a pioneering way inspired by the genius of Bitcoin and its incentive mechanisms.
Transfero Swiss’s head of Blockchain and Cryptocurrency Operations rightly highlights this innovative nature of financing. “Projects that support and promote privacy and freedoms, for the most part, suffer from serious funding problems when they do not rely directly on donations. An example is the TOR project. The Nym project, on the other hand, is not only a new technological approach but also a pioneering way inspired by the genius of Bitcoin and its incentive mechanisms. “, he says.

How Nym’s mixnet promises to ensure privacy on a blockchain
But do you know how Nym’s mixnet works? Who explains it is the co-founder and CTO of the company, Dave Hrycyszyn:
Think of a busy street you know in a big city. The street has a lot of cameras pointed at it. Surveillance camera operators are the people you’re trying to maintain your privacy against. They can see everything on the street and also record it for later analysis.
Then imagine this street full of people. Even on a busy street, it’s easy for operators to identify which paths people have followed and who they’ve talked to, since they’re recording everything on high-quality video and can play it as many times as they want.
How to defeat this surveillance? Imagine everyone wearing identical masks and clothes. Surveillance is now much more difficult. That’s what Nym technology like Sphinx does. All information traveling through Nym’s mixnet (the street, in the analogy made) is grouped into Sphinx packets. This technology makes it difficult to distinguish the information because it groups the elements that allow this distinction evenly through encryption.
Now, going back to the street analogy. Think of pedestrian traffic twice in a day. First, a Friday afternoon and then at midnight on Sunday. If you’re the only person on the street on Sunday night, surveillance cameras can still easily see what you’ve done, regardless of the disguise you’re wearing.

But if you’re part of 100 thousand people on the street on Friday afternoon, you’ll be protected. It will be very difficult for surveillance to separate you from the crowd and de-anonymize you..
Which means, in order to a tool ensures anonymity, it must put the individual together with a lot of people. The anonymity of the people in Nym’s mixnet is similar to mixing someone with a large crowd.
Still, surveillance camera operators can track people into a crowd, timing the time it takes them to do the activities and assign that time to each person. But if you put tents at regular distances in the middle of the street, the cameras can’t see inside them.
These tents are represented by us (interlaces) located in this mixnet. Nodes scramble or mix Sphinx packets to ensure that surveillance operators cannot do this individual timing.
Although people are now perfectly protected from surveillance, it is still easy to identify when they enter or leave the street – that is, when they start or stop using the mixnet. If you enter the imaginary street at the exact moment you want to counter surveillance and leave the street as soon as you’re done, it can still be pretty obvious what you’re going to do. Nym’s mixnet promises to work around this by continually sending fake traffic with which real people performing real actions can blend in. As soon as you start using it, it automatically starts sending some robots to the street as if they were you.
See how Mixnet works in practice:
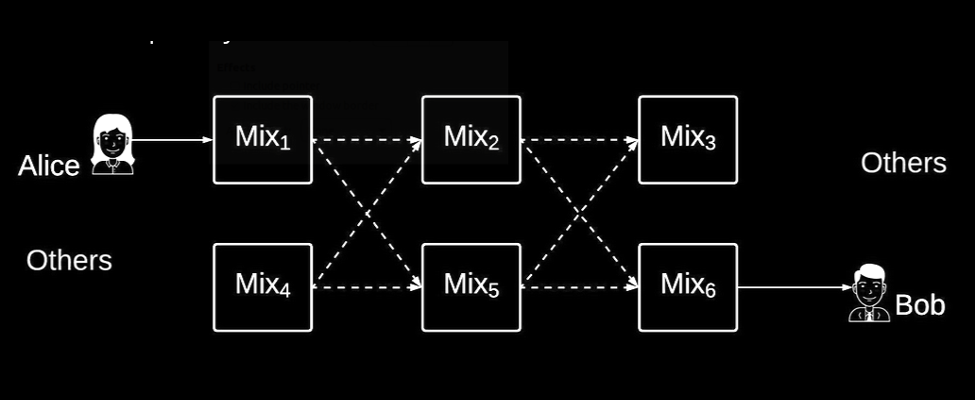
Alice’s computer, on the left, wants to send messages to Bob’s computer, through the mixnet, and avoid surveillance. As soon as her computer is turned on, it automatically starts sending Sphinx packet coverage traffic through the mixnet. Each of these packages is indistinguishable at the binary level from all other packages.
Sphinx packages are routed through mixnodes or nodes (interlaces) in the mixnet. Packets are shuffled together and issued in a different order than they were for each node. They cross multiple nodes from the mixnet and are delivered to Bob. Assuming there are sufficiently large number of people using the mixnet, it is impossible for anyone or entity to determine whether Alice was talking to Bob or even talking to someone or just automatically sending coverage traffic while she was on the street.
Mixnet uses the following techniques to defeat online surveillance:
- Makes all traffic circulating on the network to be similar
- Reorders the traffic
- Generates false traffic
With the Bitcoin, miners are rewarded for performing complex operations on the network. Similarly, in Nym’s mixnet, mixnodes or nodes will be rewarded by mixing packages that make the Internet connection work completely privately.
Mixnet source
The idea of a mixnet is not new. In 1981, David Chaum pioneered the innovative idea of a decentralized network of relays that guarantees the impossibility of communication on the Internet, concealing characteristics that allow the distinction from one content to another, the so-called metadata. Network metadata contains a large amount of sensitive information, which as a result, provides a detailed profile of the user’s online activities and associations.
A former employee of the U.S. security agency, NSA, confirms the power of metadata. “Metadata says everything about someone’s life. If you have enough metadata, you don’t really need content”, said former NSA General Counsel, Stewart Baker.
However, traditional Mixnet networks have some limitations. Those are scalability, speed, file size, latency, and vulnerabilities to attacks. But Nym claims not to adopt traditional mixnet projects. Instead, it uses a low latency anonymous communication system called Loopix, which addresses these limitations.







